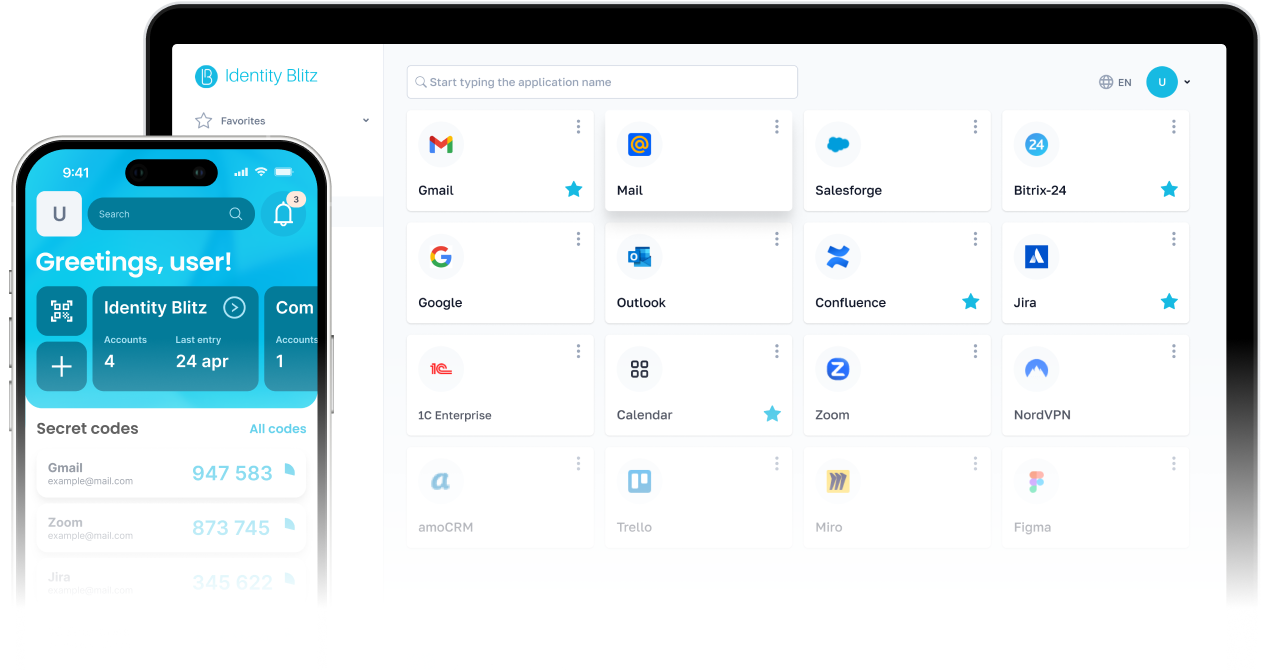
Authentication server for your organization
Blitz Identity Provider
Use only one account to log in to all of the company’s websites and mobile applications. Logging in requires authentication process – a check that the user is what he claims to be. Blitz Identity Provider makes this authentication process smoother and improves security
Blitz Identity Provider
— on-premise IAM, CIAM, SSO, and MFA solution
The product reinforces a company’s internal IT infrastructure by enhancing user account security. It supports modern authentication protocols, including OpenID Connect, OAuth 2, SAML, WS-Federation, and RADIUS, and is compatible with popular operating systems and databases
Our advantages

for all tasks

and customizable

to set up

modern standards
Questions?
Contact us for more information about product and demo.